Your privacy,
our priority
our priority
HONOR's privacy
protection philosophy
protection philosophy
Privacy is a basic right of our users, and we've made
privacy
protection a prerequisite
for all the products and services we
provide. From initial design to final delivery, we put privacy considerations into every step and give users autonomous control
over their personal information.
provide. From initial design to final delivery, we put privacy considerations into every step and give users autonomous control
over their personal information.
New privacy functions for HONOR products
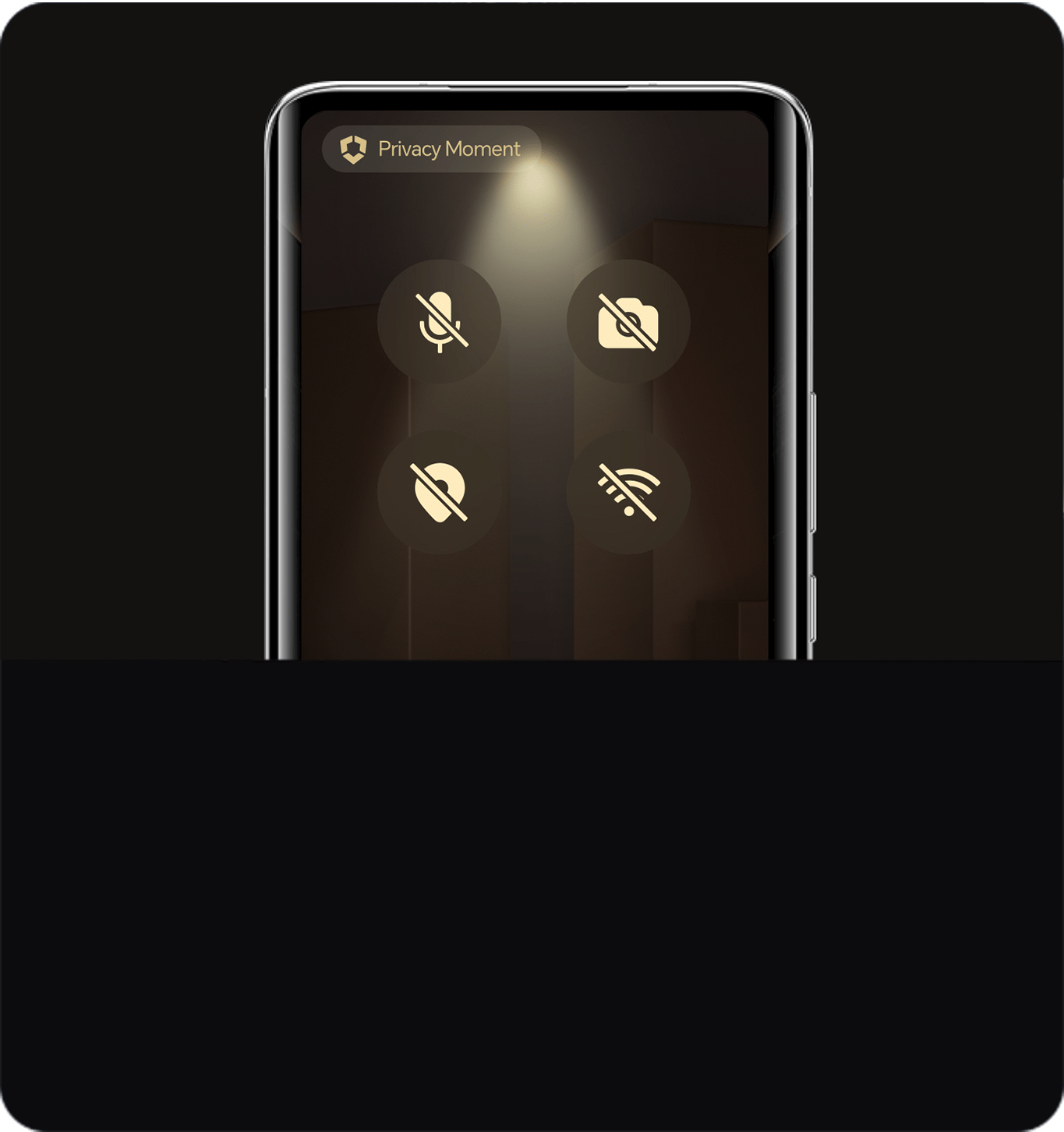
Privacy Moment prevents your device from being tracked or monitored.

Designed for security, this independent security chipset offers
hardware-level protection and secures key passwords.
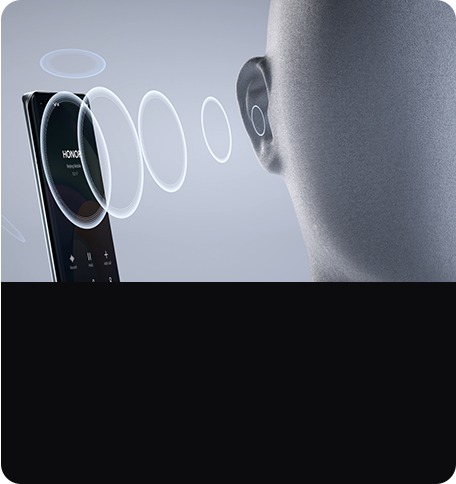
With AI privacy call, you can make your phone calls at ease without
worrying about sound leakage.
Watch the video

Use the "Discover unknown Bluetooth tag" feature to detect hidden
Bluetooth positioning devices and fend off malicious tracking.
Provide a full range of services by building on the
following five aspects of privacy protection
following five aspects of privacy protection
Protect Important Information from Being Abused
Protect Routine Use from Being Harassed
Protect Personal Data from Being Leaked
Payment Security
Secure and convenient transactions with mobile shield
Learn more 


Payment Security
Integrate the traditional USB shield into the mobile phone based on an
independent security chip and dual-TEE security OS. During bank transfer, the
digital signature certificate will be encrypted by the security chip for
storage. The self-developed HTEE (Trusted Execution Environment) ensures the
transaction is secure and trustworthy. When you enter the password, the trusted
interface protects you from tampering, screen recording, and screenshots to make
sure what you see is what you sign. The secure keyboard also helps prevent the
password from leaking.
Repair mode
Activate the "repair mode" to secure your data and keep
privacy
invisible conveniently and safely.
Learn
more



Repair mode
When you send your phone in for repairs, just set it to
repair
mode so your photos, videos, text messages, messenger apps, contacts, audio
recordings,
payment apps, and mobile banking data remains hidden from the technicians
handling your
device.
Repair mode encrypts personal data using
industry-leading
algorithms to ensure encryption strength. When this feature is enabled, repair
technicians can directly turn on the device for inspection and repairs without
needing
the lock screen password. When the repairs are done, the user can restore
protected
data by entering the lock screen password to disable repair mode.
Prevent User Behavior from
Being Tracked
Being Tracked
Position fuzzification
No matter where you are, people will only know "approximately"
where
you are.
Learn more 


Position fuzzification
Enable Fuzzy location in apps that don't need high
location
accuracy to avoid tracking.
When this feature is enabled, location data will be
fuzzified
to within 1 square kilometer for apps that do not require high location
accuracy. This
function can be used in apps such as weather and dating platforms.
Protect Personal Information
from Being Viewed
from Being Viewed
Projection privacy protection
Separate public information from the private when using screen
projection, no more worry about "social death".
Learn more 


Projection privacy protection
When projecting your phone screen to other devices, the
login
screens of apps will not be shown on the projected device by default. Also,
WeChat
messages, SMS, and other information will not be shown when projecting to HONOR
Vision
TVs.
When projecting your phone screen to PCs, tablets, and
HONOR
Vision TVs, your user name and password will not be shown if you are using the
secure
input method. When projecting to HONOR Vision TVs, chat messages will not be
shown by
default (this can be disabled if necessary).
Our five-dimensional privacy risk protection
system safeguards your privacy at all times.
system safeguards your privacy at all times.
Data minimization
Minimal personal data collection and only when necessary. Data is kept only
for as
long as necessary to achieve the purpose.
Transparency and controllability
Provide clear and unambiguous notices when collecting personal information
to
ensure that you know how it is being used. You also have the right to opt out at any time.
On-device data processing
Process and analyze data on-device whenever possible.
User identity anonymization
Use privacy-enhancing technologies to protect user identity and prevent
tracking.
Security
Use data protection technologies that are secure and reliable to safeguard
your
information.
HONOR has established a set of scientific and effective
managemental and technical systems and was awarded the most authoritative industrial certification.
ISO/IEC 27701
ISO/IEC 27701 is an international privacy protection standard jointly
published by
the International Organization for Standardization (ISO) and the International
Electrotechnical
Commission (IEC). As an extension of ISO 27001 and ISO 27002, it provides a complete
framework for
private enterprises, government agencies, non-profit organizations, and other social
organizations
regarding organizational governance, legal compliance, process regulation, information
technology,
supervision, and auditing. It is the world's first international standard for privacy
information
management and is currently the most authoritative, accepted, and applied privacy
information
management system internationally. HONOR was awarded this certification thanks to its
world-class
privacy management systems.
ISO/IEC 27001
ISO/IEC 27001 Information Security Management System is an internationally
accepted and implemented system certification standard regarding information security. By
obtaining
this certification, HONOR has demonstrated its ability to establish a scientific and
effective
information security management system that matches its developmental strategies—ensuring
that the
corresponding information security risks can be properly controlled.
Learn more about privacy and security
Note:
-The information shown on this website (privacy protection features and product privacy features) is for reference only. Please refer to the features provided in the product for accurate information. Some features may only be available in certain countries or regions.
-The information shown on this website only applies to the HONOR Magic OS and Magic UI mobile systems and certain applications. Please refer to relevant descriptions for the privacy features and functions of other HONOR products (such as PC, Tablet, and TV).
-The information shown on this website applies to HONOR phones with Magic UI 5.0 and above. Some content applies to Magic UI 3.0 and Magic UI 4.0.
If you have questions or suggestions about the information shown on this site, please click here to contact us.
-The information shown on this website (privacy protection features and product privacy features) is for reference only. Please refer to the features provided in the product for accurate information. Some features may only be available in certain countries or regions.
-The information shown on this website only applies to the HONOR Magic OS and Magic UI mobile systems and certain applications. Please refer to relevant descriptions for the privacy features and functions of other HONOR products (such as PC, Tablet, and TV).
-The information shown on this website applies to HONOR phones with Magic UI 5.0 and above. Some content applies to Magic UI 3.0 and Magic UI 4.0.
If you have questions or suggestions about the information shown on this site, please click here to contact us.